Authentication for the F5 Load-Balancers
Overview
This page describes how an F5 systems administrator (a customer with load-balanced application servers) gets a level of access (defined by a role) to the device that is limited to their partition. This ability allows them to manage their services.
! Important Note ! By design, on the F5 load balancers, a systems administrator can have access to only one partition with only one role. Please refer chapters 8, 9, and 10 in BIG-IP TMOS Concepts.pdf for more information.
- Role: the access level a systems administrator has for the set of F5 objects used by their service.
- Partition: a space on the device that the systems administrator has access to. Once inside a partition, only the F5 objects pertinent to the services deployed by that systems administrator can be viewed/modified.
- Access Policy: refer to Access Policy for Customers-Systems Administrators for more information.
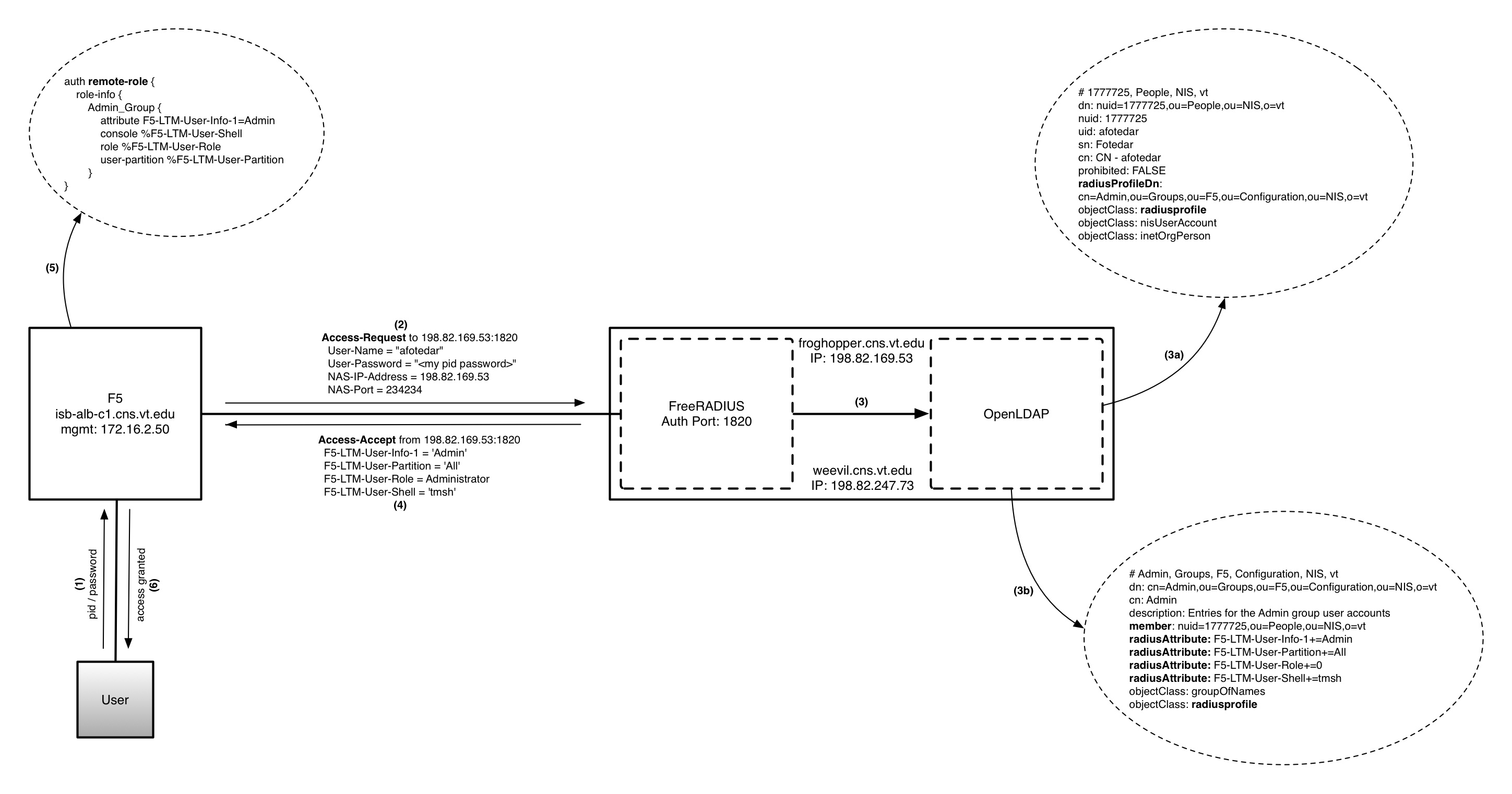
The idea is to leverage the existing AAA (Authentication, Authorization, Accounting) architecture by tweaking the FreeRADIUS and OpenLDAP servers to provide this capability.
- When F5 receives a login request from a customer, it sends an Access-Request to FreeRADIUS, which consults NI&S OpenLDAP for authorization and ED OpenLDAP for authentication.
- Assuming the authentication is successful, an Access-Accept packet is sent to the F5 with reply attributes that must match one of the remote-role groups defined on the F5.
- Once there is a match, the customer gets the appropriate role and partition access.
Remote-Role configuration on F5
auth remote-role {
role-info {
Admin_Group {
attribute F5-LTM-User-Info-1=Admin
console %F5-LTM-User-Shell
role %F5-LTM-User-Role
user-partition %F5-LTM-User-Partition
}
AppEditor_Group {
attribute F5-LTM-User-Info-1=AppEditor
console %F5-LTM-User-Shell
role %F5-LTM-User-Role
user-partition %F5-LTM-User-Partition
}
}
- A customer who needs access to the device must have a user object that is a member of one of the group objects in the NI&S OpenLDAP.
- The radiusAttribute attribute in the group objects determines the role a user has (0 in the example below is equal to Administrator. Refer to the F5 dictionary in FreeRADIUS), the partition to which s/he belongs, and whether they have tmsh (traffic management shell) access or not.
- The customer's user object must have a radiusprofile objectClass and a radiusProfileDn attribute that points to the group they belong to.
Group Object in OpenLDAP
# Admin, Groups, F5, Configuration, NIS, vt
dn: cn=Admin,ou=Groups,ou=F5,ou=Configuration,ou=NIS,o=vt
cn: Admin
description: Entries for the Admin group user accounts
member: nuid=1777725,ou=People,ou=NIS,o=vt
radiusAttribute: F5-LTM-User-Info-1+=Admin
radiusAttribute: F5-LTM-User-Partition+=All
radiusAttribute: F5-LTM-User-Role+=0
radiusAttribute: F5-LTM-User-Shell+=tmsh
objectClass: groupOfNames
objectClass: radiusprofile
# AppEditor, Groups, F5, Configuration, NIS, vt
dn: cn=AppEditor,ou=Groups,ou=F5,ou=Configuration,ou=NIS,o=vt
cn: AppEditor
description: Entries for the Application Editor group user accounts
member: nuid=1143470,ou=People,ou=NIS,o=vt
radiusAttribute: F5-LTM-User-Info-1+=AppEditor
radiusAttribute: F5-LTM-User-Partition+=Systems
radiusAttribute: F5-LTM-User-Role+=300
radiusAttribute: F5-LTM-User-Shell+=tmsh
objectClass: groupOfNames
objectClass: radiusprofile
User Objects in OpenLDAP
# 1777725, People, NIS, vt
dn: nuid=1777725,ou=People,ou=NIS,o=vt
nuid: 1777725
uid: afotedar
sn: Fotedar
cn: CN - afotedar
prohibited: FALSE
radiusProfileDn: cn=Admin,ou=Groups,ou=F5,ou=Configuration,ou=NIS,o=vt
objectClass: radiusprofile
objectClass: nisUserAccount
objectClass: inetOrgPerson
# 1143470, People, NIS, vt
dn: nuid=1143470,ou=People,ou=NIS,o=vt
nuid: 1143470
uid: stlee
sn: Lee
cn: CN - stlee
prohibited: FALSE
radiusProfileDn: cn=AppEditor,ou=Groups,ou=F5,ou=Configuration,ou=NIS,o=vt
objectClass: radiusprofile
objectClass: nisUserAccount
objectClass: inetOrgPerson
- FreeRADIUS's load-balancing instance is setup for role-based access. The Access-Accept packet must have the reply attributes below.
- For more information on how FreeRADIUS should be set up, see Using F5 vendor-specific attributes with RADIUS authentication.
Radtest from Cricket's FreeRADIUS server
radius@cricket(load-balancing):~
$ radtest afotedar <my pid password> 198.82.169.53:1820 234234 <shared secret
in clients.conf>
Sending Access-Request of id 81 to 198.82.169.53:1820
User-Name = "afotedar"
User-Password = "<my pid password>"
NAS-IP-Address = 198.82.169.53
NAS-Port = 234234
Message-Authenticator = 0x00
rad_recv: Access-Accept packet from host 198.82.169.53:1820, id=81, length=68
F5-LTM-User-Info-1 = 'Admin'
F5-LTM-User-Partition = 'All'
F5-LTM-User-Role = Administrator
F5-LTM-User-Shell = 'tmsh'